The Temptation of Generalized Surveillance
From Orwell to Snowden, the slippery slope towards Chinese-style surveillance in democracies
Note : After the 14-part series in which we looked at how nation-states are being disrupted by the Internet and globalization, and a 4-part series on why now is the worst time for them, I have concluded that there are two main ways for governments to respond to these disruptions:
Increasingly control what their residents do, via permanent digital surveillance and the use of AI and machine learning (China's way)
Accept that their role will diminish and treat their residents more like customers
In this new series, corresponding to chapter 4 of my forthcoming book, we analyze the (very) slippery slope towards generalized surveillance to which many countries, including the most democratic, are committing themselves.
Here are the 11 articles of the series :
"Power tends to corrupt; absolute power corrupts absolutely."
- Lord Acton, historian
"The hearts of men are easily corrupted, and the ring of power has a mind of its own."
- Galadriel, Lord of the Rings.
We saw in the second series the extent to which the Internet is disrupting nation-states, undermining many of their fundamental powers.
But computers and networks also increase the power of nation-states in certain cases.
We'll look at which ones, why their use erodes the fundamental freedoms that are supposed to underpin Western democracies, and why nation-states are strongly tempted to use them.
The power to monitor all Internet interactions more easily
"With the development of television, and the technical advance which made it possible to receive and transmit simultaneously on the same instrument, private life came to an end.
Every citizen, or at least every citizen important enough to be worth watching, could be kept for twenty four hours a day under the eyes of the police."
George Orwell, 1984
Digital has a huge advantage over analog: it's very easy to copy data for analysis.
And governments, even the most democratic ones that are supposed to set an example, have a field day.
I've already mentioned Edward Snowden in the section on exiles of “How the Internet prevents governments from enforcing their laws”.

In 2013, a former CIA employee, he had been working for the NSA for 4 years via Dell, which was a subcontractor.
He had access to tens of thousands of documents through his job as a system administrator, and was increasingly revolted by what he saw: widespread surveillance of Americans (and the world), which he felt was contrary to the fundamental rights supposedly guaranteed by democracies, and the American constitution in particular.
Then came the final straw: in March 2013, during a session of the U.S. Senate Select Committee on Intelligence, Senator Ron Wyden asked then-U.S. Director of National Intelligence James Clapper, "Is the NSA collecting data on millions or hundreds of millions of Americans?", to which Clapper replied, "No [...] Not knowingly. There are cases where data might inadvertently, perhaps, be collected, but not knowingly1 ".
When he heard this, Snowden saw red: he knew that his boss had just lied to the Senate, because he had seen in the documents to which he had access that, on the contrary, the NSA was knowingly collecting data on hundreds of millions of Americans!
This convinced him that this surveillance of the population was illegal, even unconstitutional, and he decided to go public.
He copied all the documents he could - probably over a million2 - and began sending hundreds of them to journalists around the world, then went to Hong Kong just as the first articles were being published.
Revelations about widespread digital surveillance
And the revelations the journalists made based on their analysis of these documents were... intense. Judge for yourself, for at the time of the revelations :
The NSA is harvesting millions of e-mail and instant messaging contact lists3 .
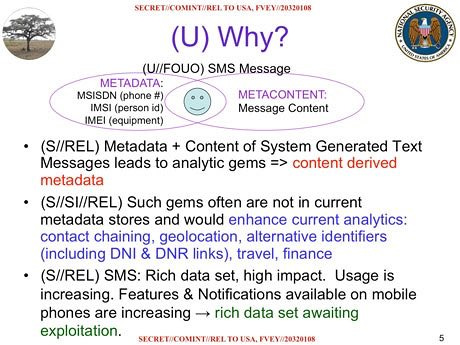
It intercepts 200 million SMS per day, which it is able to view in clear text, worldwide4 , which enables it, among other things:
Know who knows who, thanks to SMS messages sent automatically when a call is missed, at a rate of 5 million messages a day.
Track people's cross-border movements, thanks to SMS messages sent by telephone companies when they arrive in a new country, with 1.6 million messages per day.
Learn 110,000 names a day, thanks to business cards sent by SMS
800,000 financial transactions per day
And *all* the content of messages, allowing keyword searches for example, or revealing messages sent and received by a particular target, going back months or years.5
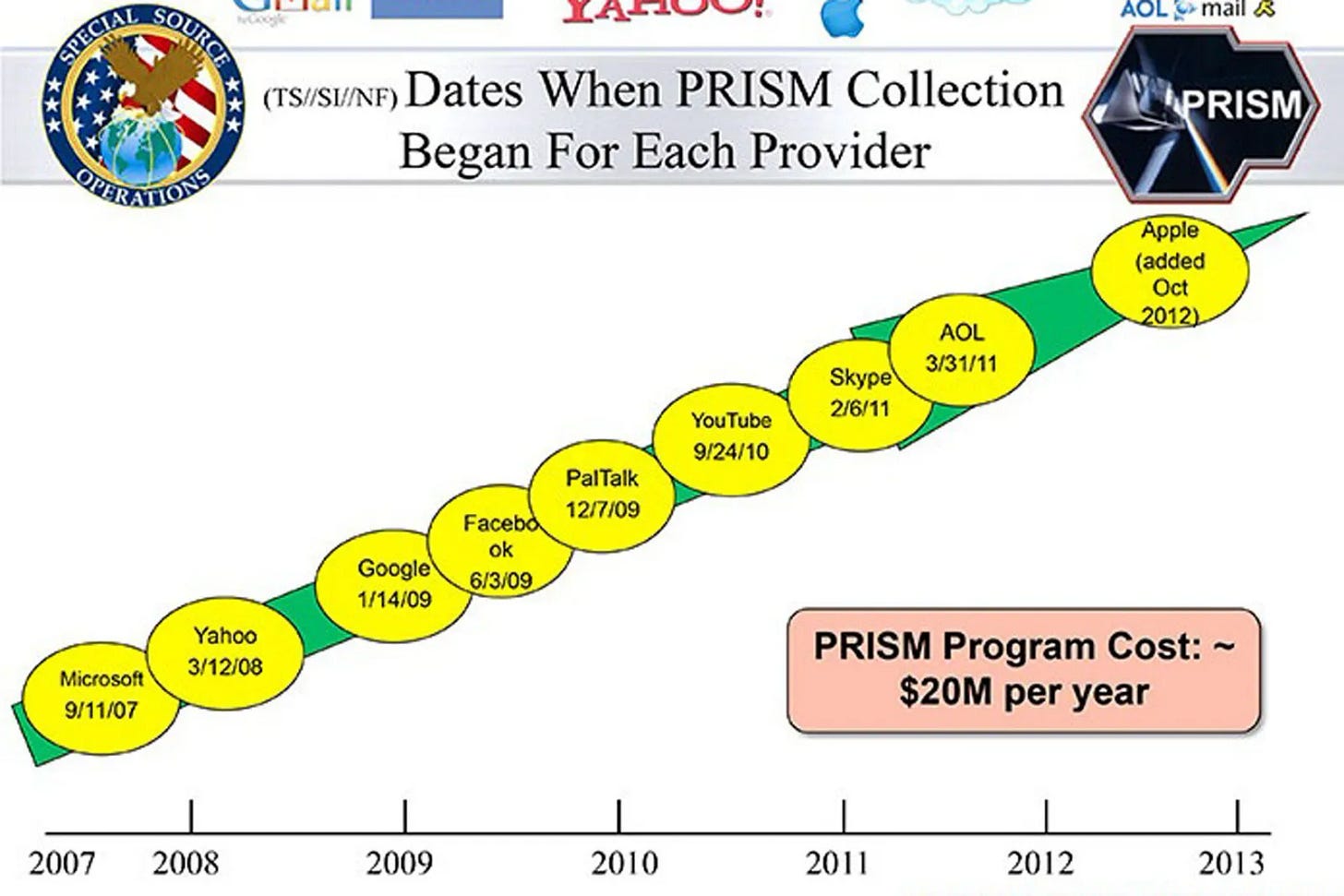
It connects directly to the central servers of nine major US Internet companies (Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, Apple) extracting audio and video conversations, photographs, emails, documents and connection logs6 , and others like Dropbox are planned in the near future7 .
It tracks and maps the location of cell phones worldwide... at a rate of 5 billion records per day8 ! This enables the NSA to find out who's dating whom, on a global scale: who you spend the most time with, where you go, how often, etc., by analyzing phones that move together by connecting to the same base stations.
In partnership with its British counterpart GCHQ, it uses data from dozens of smartphone applications to harvest metadata that can be used to identify people, such as current location (via geolocation), age, gender, zip code, marital status, income, ethnic origin, sexual orientation, level of education, number of children, etc.9 , to the point where a report from the British agency bluntly stated that "anyone using Google Maps on a smartphone is working to help [the agency's] intelligence system ".10
The British agency GCHQ, in partnership with the NSA, intercepted and stored the webcam images of millions of Internet users captured during conversations on Yahoo without them being suspected of anything. Many of these conversations were sexually explicit, between spouses. One of the purposes of this operation was to train automatic facial recognition software11 .
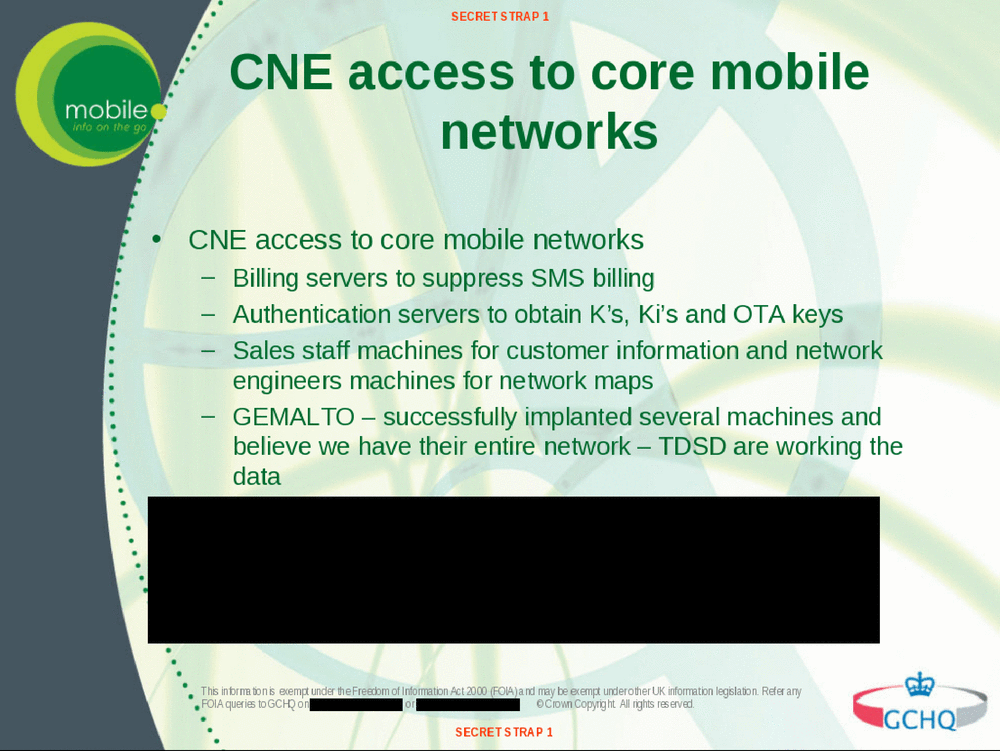
The two agencies have also penetrated the systems of the Dutch company Gemalto, which produces two billion SIM cards every year for operators worldwide. This hack enables them to steal the 3G and 4G security keys of millions of SIM cards, so that they can monitor mobile communications without seeking or receiving authorization from telecommunications companies and foreign governments12 .
The NSA has infected between 85,000 and 100,000 computers with malware on an automated basis, just in case it might prove useful, and plans to increase to millions eventually13 .
It secretly accesses Yahoo and Google data centers to collect information on hundreds of millions of account holders worldwide by tapping undersea cables used by these companies14 . The Washington Post reporter points out, "Such large-scale collection of Internet content would be illegal in the U.S., but the operations take place overseas, where the NSA is authorized to assume that anyone using a foreign data link is a foreigner."
Of course, there were still millions of Americans caught in the net. But you'll notice something interesting here: the US administration is also using the separation between location and data that the Internet enables to hack the system!
It records all telephone conversations of all residents - and visitors - to the Bahamas, thanks to the installation of a backdoor in the country's cell phone network, for 30 rolling days.
And it's not doing it to catch terrorists (which is its primary mission, along with surveillance of hostile foreign governments) but to combat drug trafficking.
The backdoor was installed thanks to cooperation with the DEA, the US drug enforcement agency, which negotiates with foreign governments for case-by-case surveillance of suspected drug traffickers.
But these governments have no idea that the equipment installed for this purpose can be misused by the NSA to monitor their entire population, not just a few individuals.
And to accomplish this mission of fighting drug trafficking - which is not one of its attributes - it engages not only in mass surveillance of an entire population, made up overwhelmingly of innocent people, but also of many Americans who have a second or main residence there, and who live in a democracy and under the rule of law.
This small country probably represents a test of the system for the NSA, before its deployment in other countries15 .
It cooperates closely with the secret services of other countries. In another example of "hacking" the system, since intelligence agencies in democratic countries are not allowed to monitor their own populations, they make a friendly arrangement: they give data concerning their own population to an agency in another country, so that the foreign agency can freely analyze the data, and pass on any interesting information to the agency that shared it!
For example, the French intelligence services gave the NSA 70.3 million phone records collected in France between December 10, 2012 and January 8, 2013 alone16 .
Remember the 200 million SMS messages collected per day by the NSA that I mentioned earlier? That included millions of British SMS messages. GCHQ, the British equivalent of the NSA, had access to this database, and could therefore search millions of domestic messages, whereas without this access they would have had to make legal requests to British telephone operators. This partnership with the NSA enabled them to circumvent the law. The British agents can only consult the metadata, and not the content of the SMS, but to do so, they must not forget to click on the right button to activate the option not to see the content17 !
Of course, we hope they don't forget to click the button too often.
The NSA has deliberately weakened the encryption protocols used: "The SIGINT Enabling project actively engages the U.S. and foreign computer industries to covertly influence and/or overtly exploit the designs of their commercial products [by inserting] vulnerabilities into commercial encryption systems, computer systems, networks and communication devices used by the targets" tells us directly from the document18 stolen by Snowden.
This is all the more serious given that, in the 90s, the NSA promoted the "Clipper chip", an encryption chip with an official backdoor that was supposed to give governments and law enforcement agencies access to encrypted data, but lost this battle: the law intended to force companies and users to use this chip was never passed, and the market rejected it. When the NSA realized its failure, it tried to achieve the same goal, but by stealth, by corrupting security protocols and the companies responsible for implementing them19 .
The NSA has thus bypassed a democratic process when it has not been in its favor, implementing what it wanted by devious means20 .
The NSA and other foreign agencies use free airport wifi to track people, and trace their movements after they leave the airport, thanks to the identification information collected21 .
Some NSA employees were using the capacity of their tools to spy on their spouses, a practice that was indeed officially forbidden, but those who were discovered doing so were, in the worst cases, given little administrative sanction22 .
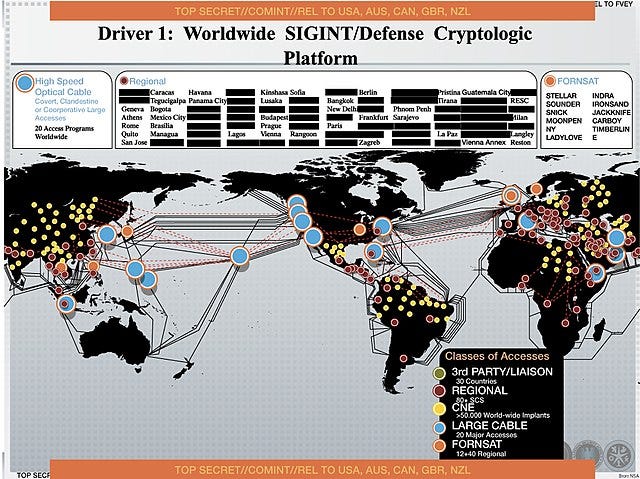
And it's not just the Americans. For example, GCHQ, the British equivalent of the NSA, has forced many telephone operators to give it access to undersea fiber-optic cables, giving it access to the majority of Internet and telephone communications circulating in Europe, enabling it to listen in on telephone calls, read e-mails and text messages, and see which websites Internet users around the world are visiting. It can also store and analyze virtually all European Internet traffic23 .
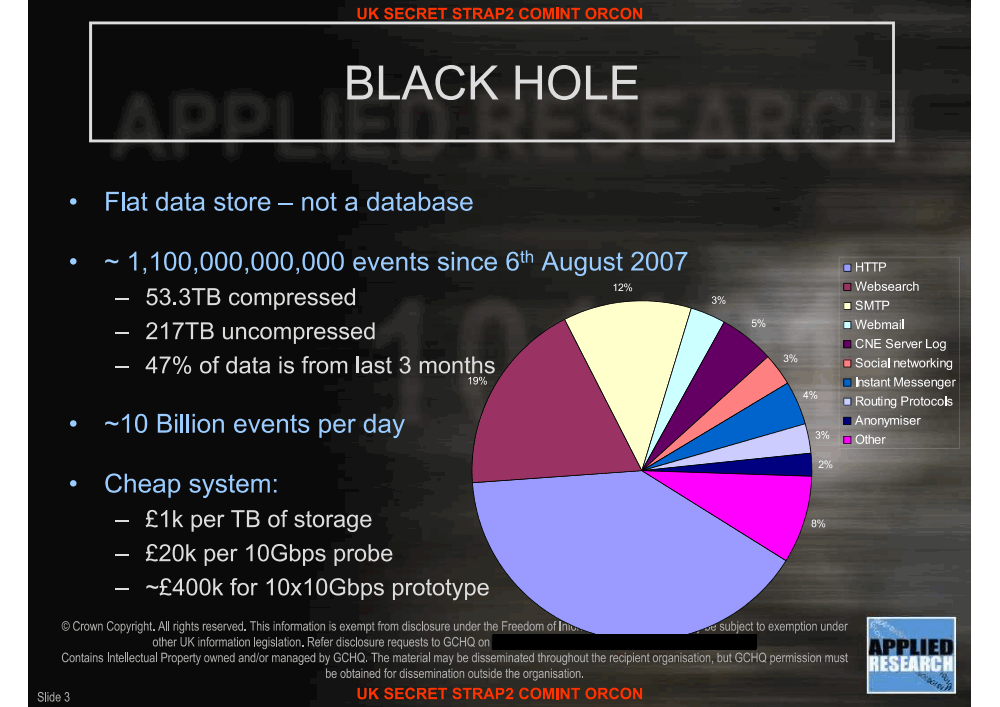
GCHQ has also developed a system to "profile the browsing habits of every visible user on the Internet" and stores 50 billion metadata per day for this purpose, with plans to increase this capacity to 100 billion per day by the end of 201224 .
Agencies in virtually all democratic countries engage in mass surveillance:
Along with the USA and Great Britain, Canada, Australia and New Zealand cooperate closely in a system known as the "Five Eyes"25 .
Germany26 , France27 , Spain, Sweden28 , the Netherlands, Norway, Belgium, Italy, Denmark29 , Switzerland and Israel30 . In fact, it's hard to find a Western democratic country that doesn't engage in mass surveillance.
This surveillance certainly affects primarily non-Americans, but Snowden was right, and Clapper did lie to the Senate, judge for yourself:
The NSA is demanding that the American telephone operator Verizon - which in 2013 was 1st on the market with 116 million customers31 - provide it, on a "daily and permanent basis", with metadata on all telephone calls made through its systems, both in the USA and between the USA and other countries32 .
What's more, two years after these discoveries, the New York Times revealed that the telephone operator AT&T was cooperating closely with the NSA, to the extent that the agency praised the company's "extreme willingness to help", even though it was "a partnership, not a contractual relationship". Among other things, this "partnership" enabled the NSA to access billions of emails between 2003 and 2013, as well as the metadata of 1.1 billion calls per day from 201133 .
The NSA has built a surveillance network capable of monitoring approximately 75% of American Internet traffic34 .
An analysis of 160,000 emails and text messages intercepted by the NSA between 2009 and 2012 showed that 90% of the people monitored should not have been, and that almost half were Americans35 .
What metadata can tell us about you
You'll note that these surveillance programs sometimes give access to the content exchanged (the analysis of video chats on Yahoo, the tapping of all telephone conversations in the Bahamas, etc.), and sometimes just to the metadata (those of American Verizon subscribers, the 5 billion recordings per day of the movements of hundreds of millions of people around the world via their cell phones, etc.).
To be very clear, content is what was is said in a telephone conversation, or the content of a text message.
Metadata is about who talks to whom (or who visits which website and uses which service), when, how often, and with what volume of exchanges.
For example, if you're one of WhatsApp's two billion active users, and someone gets their hands on your metadata (but not the content of the conversations), then they'll know :
Which numbers do you trade with
How often
The volume of the data, which can indicate whether you're exchanging photos, audio or video (videos take up much more space than text or even photos, photos take up an intermediate space between text and video, etc.).
And believe it or not, this can reveal a lot about you, especially if the phone numbers of people you exchange with can be easily attributed to people or institutions.
Let's take another example: your telephone conversations. Imagine that a hacker, a government or some other malicious person has access to their metadata, but not to the content of the conversations. What kind of information could they deduce about your life?
Here are some classic examples36 :
They know you called a phone sex number at 2:24 a.m. and talked for 18 minutes. But they don't know what you talked about.
They know you called the suicide prevention hotline from the Golden Gate Bridge. But the subject of the call remains a secret.
They know that you received a call from an HIV testing service, then that you called your doctor, then that you visited the website of an HIV support group within the same hour. But they don't know what you talked about on the phone.
They know you called a gynecologist, talked for half an hour, then called the number for the local abortion clinic later that day.
Are you beginning to understand just how massive an invasion of your privacy this metadata can be? And it's even more so if the metadata recovered is not just about WhatsApp or your calls, but about your entire digital life: by correlating which sites you visit, which web services you use, with whom you exchange emails and other messages via other applications, it's possible to know an awful lot about you.
This is all the more true if it's a government that has access to this information and uses digital tools to analyze all this data.
And if you tell yourself that your government is democratic and that you live under the rule of law, consider that :
Entire sections of these surveillance programs have been declared illegal, as we shall see shortly.
That the distinction between a democratic and a non-democratic country is not binary: there is a gradient with millions of nuances between "absolute dictatorship" and "absolute democracy". And that generalized surveillance is tempting for all governments, and that it's a slippery slope.
And not everyone is lucky enough to live in a free country.
The political and legal response
Faced with the scale of the revelations, U.S. Director of National Intelligence James Clapper had to backtrack on his statements, and admitted that he had indeed lied to senators37 .

President Barack Obama, who had promised during his 2008 campaign that he would preside over "the most transparent administration in U.S. history" and that there would be "no more secrecy, that is a commitment that I make to you.", found himself quite embarrassed by the affair38 . After initially downplaying the problems and the scope of the surveillance program, he eventually acknowledged the dangers that NSA surveillance represents for civil liberties, and promised reforms39 .
He also created a 5-member commission of inquiry, including a former CIA official, which was tasked with proposing recommendations to improve the safeguards of these surveillance programs: they made 46 proposals40 .
Republican Representative Jim Sensenbrenner, who was one of the main instigators of the Patriot ACT passed after the attacks of September 11, 2001, declared in 2014 that the government had performed "feats of legal gymnastics" to use the Patriot Act as a starting point for this mass surveillance program. "I don't blame people for losing trust in their government, because their government has betrayed their trust," he said41 .
A weak legislative answer
The U.S. Senate eventually passed the USA Freedom Act to correct the NSA's most flagrant excesses of power, but in a rather timid manner: many of the 46 proposals of the investigative committee were not implemented, and it was a considerably weakened version of the law that was passed, compared to the compromise version that had been unanimously approved by the Judiciary and Intelligence Committees42 .
Privacy groups withdrew their support for this watered-down version, concluding that, while it was a step in the right direction, there was still too much legal vagueness to really effectively limit the powers of the NSA and other intelligence agencies43 .
Several years later, the U.S. Court of Appeals for the Ninth Circuit, regarding a terrorist financing case, declared that the warrantless collection of millions of Americans' phone record metadata violated the Foreign Intelligence Surveillance Act and may well be unconstitutional44 .
The 4 defendants in this story, 4 Somali refugees who became naturalized U.S. citizens, had been sentenced to between 6 and 18 years in prison for sending around $10,000 to a Somali terrorist organization.
In the wake of the Snowden revelations, the US government shared with the press that the men's indictment had been made possible by the collection of data on millions of Americans.
Among other arguments, the defendants therefore asked for the judgment to be set aside, arguing that this collection of information was illegal, and that they could not have been charged without it.
But while the court of appeal did indeed declare the program illegal, after analyzing the data collected, it found that this data had had no impact on the indictment and conviction of the defendants, which was in direct contradiction to what the government representatives were saying45 .
So: this domestic surveillance program was not only illegal, it was useless. Because the US government could not account for a single terrorist arrested thanks to this program46 .
These two main points - illegality and uselessness - were also the conclusion of the very official U.S. Privacy and Civil Liberties Oversight Commission, in its 2014 report47 .
This is a clear and proven example of an illegal mass surveillance program that was set up for stated reasons (the fight against terrorism), without ever really examining the effectiveness of the systems in relation to their stated objectives, by "the land of the free", a democratic country which is supposed to be not only exemplary, but among the most exemplary, and which has suffered a severe loss of image, legitimacy and soft power as a result of these revelations.

And if effectiveness isn't really measured, it's probably because states ideally want to have as much information as possible on their population, and they use and will use the best excuse of the moment to do so - at the moment, the fight against terrorism or the protection of children.
Coming soon...
In the next article, we'll see that these revelations, while sinister on the whole, still brought their share of good news about certain technologies that were blocking intelligence services, and we'll examine the reaction of civil society, and similar programs set up in other democratic countries.
In the meantime, feel free to follow Disruptive Horizons on Twitter, and join the tribe of Intelligent Rebels by subscribing to the newsletter :
Other articles in the series
"Pentagon Says Snowden Took Most U.S. Secrets Ever: Rogers", Chris Strohm, Bloomberg, 2014
"NSA collects millions of e-mail address books globally", Barton Gellman , The Washington Post, 2013
"Report: NSA collected 200m texts per day", BBC, 2014
"NSA collects millions of text messages daily in 'untargeted' global sweep", James Ball, The Guardian, 2014
"U.S., British intelligence mining data from nine U.S. Internet companies in broad secret program", Barton Gellman, The Washington Post, 2013
"NSA Prism program taps in to user data of Apple, Google and others", Glenn Greenwald, The Guardian, 2013
"NSA tracking cellphone locations worldwide, Snowden documents show", Barton Gellman, Washington Post, 2013
"Spy Agencies Tap Data Streaming From Phone Apps", James Glanz, The New York Times, 2014
See footnote 9
"Optic Nerve: millions of Yahoo webcam images intercepted by GCHQ", Spencer Ackerman, The Guardian, 2014
"How Spies Stole The Keys To The Encryption Castle", Jeremy Scahill, The Intercept, 2015
"How the NSA plans to infect 'millions' of computers with malware", Ryan Gallagher and Glenn Greenwald, The Intercept, 2014
"NSA infiltrates links to Yahoo, Google data centers worldwide, Snowden documents say", Barton Gellman, Washington Post, 2013
"Data Pirates of the Caribbean: The NSA Is Recording Every Cell Phone Call in the Bahamas," Ryan Devereaux, The Intercept, 2014
"Surveillance : la DGSE a transmis des données à la NSA américaine", Jacques Follorou, Le Monde, 2013
"Revealed: UK and US spied on text messages from Brits", Geoff White, Channel 4, 2014
"Computer network operations SIGINT enabling", NSA, 2013
"N.S.A. Able to Foil Basic Safeguards of Privacy on Web", Nicole Perlroth, The New-York Times, 2013
"The NSA is Making Us All Less Safe", Cindy Cohn, EFF, 2013
"CSEC used airport Wi-Fi to track Canadian travellers: Edward Snowden documents", Greg Weston, 2014
"NSA Officers Spy on Love Interests", Siobhan Gorman, The Wall Street Journal, 2013
"British Officials Have Far-Reaching Access To Internet And Telephone Communications", John Goetz, Süddeutsche Zeitung International, 2013
"PROFILED - From Radio to Porn, British Spies Track Web Users' Online Identities" , Ryan Gallagher, The Intercept, 2015
"History of 5-Eyes - explainer", Paul Farrell, The Guardian, 2013
"Transfers from Germany Aid US Surveillance", Von Hubert Gude, Der Spiegel 2013
"La France, précieux partenaire de l'espionnage de la NSA", Jacques Follorou, Le Monde, 2013
"GCHQ and European spy agencies worked together on mass surveillance", Julian Borger, The Guardian, 2013
"Denmark is one of the NSA's '9-Eyes'", Justin Cremer, The Copenhagen Post, 2013
"NSA shares raw intelligence including Americans' data with Israel", Glenn Greenwald, The Guardian, 2013
"NSA collecting phone records of millions of Verizon customers daily", Glenn Greenwald, The Guardian, 2013
"AT&T Helped U.S. Spy on Internet on a Vast Scale," Julia Angwin, The New York Times, 2015
"New Details Show Broader NSA Surveillance Reach", Siobhan Gorman, The Wall Street Journal, 2013
"In NSA-intercepted data, those not targeted far outnumber the foreigners who are", Barton Gellman, The Washington Post, 2013
All these examples are taken from "Why Metadata Matters" by the Electronic Frontier Foundation, 2019
"National Intelligence Director Apologizes for Lying to Congress," Paul D. Shinkman, US News, 2013
"Obama on Mass Government Surveillance, Then and Now," Jason M. Breslow, PBS, 2014,
"The President on Mass Surveillance", The New York Times, 2014
"Liberty And Security In A Changing World”, Richard A. Clarke et al, 2013
"NSA reform bill passes House, despite loss of support from privacy advocates", Andrea Peterson, The Washington Post, 2014
"The Weakened USA FREEDOM Act", Kevin Bankston, 2014
"Bulk Call Details Records Collection Ends: What that Means", David Greene, Electronic Frontier Foundation, 2015
"NSA surveillance exposed by Snowden was illegal, court rules seven years on", The Guardian, 2020
"Declassified Report Shows Doubts About Value of N.S.A.'s Warrantless Spying," Charlie Savage, The New-York Times, 2015
"Report on the Telephone Records Program Conducted under Section 215 of the USA PATRIOT Act and on the Operations of the Foreign Intelligence Surveillance Court," Privacy and Civil Liberties Oversight Board, 2014.











I've been thinking a lot about this. At dinner parties, I'll often hear friends joke, "don't pay any attention to that Siri!" There's this awareness that we are being surveilled and a kind of irreverence to it. It's like "I'm not doing anything wrong so listen all you like!" I have to admit I feel some of that myself. If surveillance is being used to find and capture actual bad guys (terrorists, sex traffickers, murders etc.) I feel like by all means go ahead. But if it starts to be used for the examples you mentioned (catching women looking for an abortion), that's not ok. So the question in my mind is: how to we ensure personal data is being used for good, not evil? Which governments can/can't be trusted with this technology?