The Good News about the Snowden Revelations
Bastions of Digital Freedom against Government Espionage
Note : After the 14-part series in which we looked at how nation-states are being disrupted by the Internet and globalization, and a 4-part series on why now is the worst time for them, I have concluded that there are two main ways for governments to respond to these disruptions:
Increasingly control what their residents do, via permanent digital surveillance and the use of AI and machine learning (China's way)
Accept that their role will diminish and treat their residents more like customers
In this new series, corresponding to chapter 4 of my forthcoming book, we analyze the (very) slippery slope towards generalized surveillance to which many countries, including the most democratic, are committing themselves.
Here are the 11 articles of the series :
Because yes, there were good news among all those sinister revelations: the NSA wasn't able to crack encryption when it was being used properly, notably with open source tools that hadn't been compromised like commercial tools.
In particular, the NSA indicated that it had a lot of difficulty in 2012 with people using :
Tor, a browser that uses a communication protocol1 that hides where users are and what they're doing.
Tor was originally developed with the support of the U.S. Naval Research Laboratory, which demonstrates a major contradiction that nation-states suffer from: governments would ideally like to be able to break encryptions when they want, while having protocols that are unbreakable by adversaries the rest of the time. This is obviously impossible, and results in contradictory actions, as here a program built with the support of one branch of government, which becomes a problem for another branch of government.
TrueCrypt (now replaced by Veracrypt) an open source file and hard disk encryption program, which I mentioned in “How encryption is disrupting nation-states”.
PGP, an email encryption software that has been around since 1991, was a major player in the "encryption war" of the 1990s against the Clipper chip, which contained an official backdoor that I mentioned earlier2 .
ZRTP, an encryption protocol for real-time communications, used in particular by Signal until 2017, when it was replaced by the even more secure Signal protocol (now used in particular by WhatsApp).
I'll come back to these tools, or rather their modern equivalent, in the articles on computer security.
The fact that encryption was becoming more and more widely used was also a problem.
One of the NSA documents thus stated, "20 years ago, the mere fact that a communication was encrypted meant that it was very likely to contain foreign intelligence information, as only governments and other important targets had the resources [to set up] encrypted communications," and that now [around 2012], the spread of encryption on the web makes this less and less true3 ".
Civil society's response
Following these revelations, millions of people were outraged, including major Internet companies who discovered that the NSA was shamelessly tapping into their data.
It was an electroshock that shook the entire IT industry, and a realization: this mass surveillance was largely permissible because, at the time, the majority of Internet traffic was unencrypted.
Remember the 5th principle "An inversion of the balance of power between attack and defense technologies is highly disruptive for the powers that be"... and the fact that encryption is precisely an inversion of the balance of power, because it makes defense much easier than attack, as we saw in “How encryption is disrupting nation-states” ?
So communications had to be encrypted to make them impenetrable to the ears of the NSA and other data-hungry agencies, and also to make the mere fact of using encryption less suspect, to make it the new norm.
This achievement triggered a vast movement to encrypt all Internet traffic:
In 2013, Google stated that, all other things being equal, a site would rank higher in its rankings if it were encrypted, motivating millions of companies to encrypt their sites in order to rank higher.
The Let's Encrypt association was founded (and financed by the Who's Who of GAFAS... and associations defending freedoms) in 2014 to offer a free SSL certificate4 to any site owner who requested it, which has led to an explosion in the number of encrypted sites because certificates used to be complicated and expensive to produce5
GAFAM have gradually moved from encrypting only sensitive pages, such as payment pages, to encrypting their entire6 sites. Millions of other sites followed suit.
Apple required apps to connect to the Internet via an encrypted connection, rather than in cleartext.
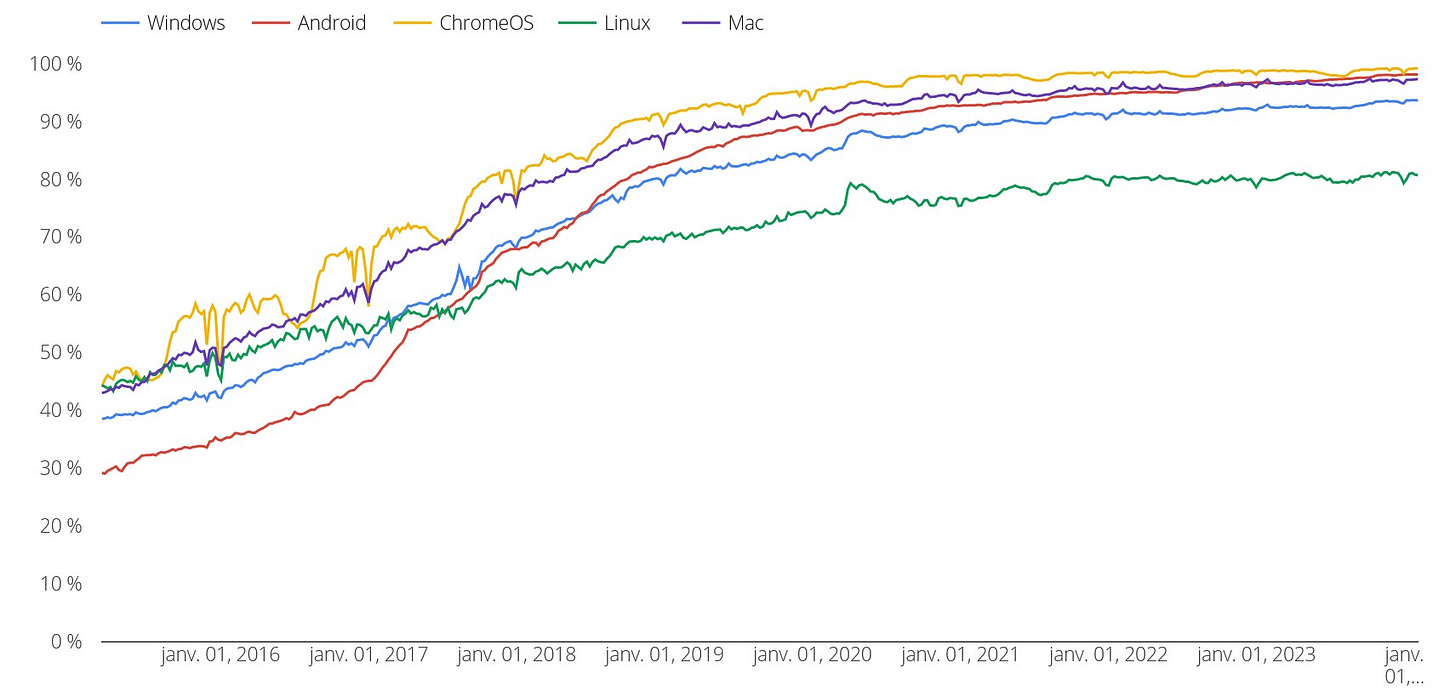
And it worked: encrypted web traffic rose from less than 50% in early 2014, to half in 20177 , and reached 95% by 20228 , making the Internet far less susceptible to mass surveillance.
And now, it's almost suspicious not to use encryption, rather than the other way around!
Either way, by using encrypted communications, you blend into the crowd, and that's a real victory against the prying ears of data-hungry governments.
New tools to the rescue
In addition, numerous tools have also been created or improved to enable end-to-end encrypted communications and data9 , offering additional security against hackers or overly intrusive governments:
Signal, a program similar to WhatsApp that uses the protocol of the same name to encrypt all communications and information exchanges from end to end.
Unlike WhatsApp, Signal doesn't store any metadata, apart from the date your account was created, and the phone number used to create it.
WhatsApp also uses the Signal protocol to encrypt communications and data exchanges, but the backup of your messages (in iCloud or Google Cloud) is by default not end-to-end encrypted: a hacker, or a government, could therefore access it.
Standard Notes is end-to-end encrypted, unlike its equivalent, Evernote.
Protonmail, end-to-end email encryption
Sync.com10, the end-to-end encrypted version of Dropbox, which also allows you to securely back up photos from your smartphone.
Etc. The list goes on and on! And we'll go into more detail in the section on computer security.
But I've got nothing to hide!
Maybe you've read all this and thought something like "But I've got nothing to hide! The NSA can go digging through my digital life, it doesn't matter! All these actions are pointless."
If this applies to you, I have several points to make:
1st point: imagine if you applied this reasoning to other principles
"Religious freedom? But there's no point, I've only got one religion, I don't need to be free to change it. It's useless."
"Freedom of expression? But there's no point, I've got nothing special to say. It's useless."
"The right to strike? But there's no point, I've got nothing to protest against right now. It's useless."
Etc. etc. See what I mean?
"If you think privacy isn't important to you because you have nothing to hide, you might as well say free speech isn't important to you because you have nothing useful to say."
Edward Snowden
If you disagree, I invite you to reread 198411 and ask yourself whether you would feel comfortable enough expressing ideas that might go against the government in an environment where you don't know whether you're being spied on right now or not.
Because, if you don't use the appropriate encryption methods, I guarantee you that this is exactly what's happening: you may or may not be being monitored. You don't know that, but you do know that your government has the technical capability to do so, and that, barring extraordinary circumstances, it has already demonstrated its willingness to use it in the past.
2nd point: it's not just about access to your data by the intelligence agencies of democratic governments.
But also by criminals, hackers and agencies of governments with little or no democracy.
3rd point: I take you at your word :)
If you really have nothing to hide, I'll take your word for it!
Please send the following documents to email [at] olivier-roland.com :
Access to your Dropbox, Google Drive or equivalent folders
Access to all your e-mail addresses
Access to all your photos
A PDF of your latest bank statements (say, for the last 6 months)
I will then publish these documents on my website, for all to enjoy.
If you're using password management software like Bitwarden or 1password, you can send me your access details so that I can wander freely through all the web service accounts you've created.
Do you dare? Go for it! :)
And if you're not ready to do this, ask yourself: okay, you've got nothing to hide, but really? So much so that you don't even raise an eyebrow at the idea of seeing all your personal data roaming freely on the web?
I'll be sharing the number of people who have taken up this challenge, along with links so readers can access their voluntarily shared data.
Coming soon...
In the next article, we'll see that the USA is far from alone in its mass surveillance programs, and that many democratic countries are also involved.
In the meantime, feel free to follow Disruptive Horizons on Twitter, and join the tribe of Intelligent Rebels by subscribing to the newsletter :
Other articles in the series
Onion routing". This is no joke :)
"New documents reveal which encryption tools the NSA couldn't crack", Russel Brandom, The Verge, 2014
"Inside the NSA's War on Internet Security", Der Spiegel, 2014
Necessary for encrypting traffic between a website and the user
Yours truly encrypted all his sites in 2015, when Let's Encrypt became compatible with my hosting provider.
"Google encrypts data amid backlash against NSA spying", Craig Timberg, 2013
"We're Halfway to Encrypting the Entire Web," Gennie Gebhart, EFF, 2017
"HTTPS encryption on the web", Google Transparency Report, 2022
End-to-end encryption means that even Signal doesn't have the decryption key - it's only on your devices.
By going to https://olivier-roland.com/sync/ , you earn 1 extra GB for your account (and you earn me 1 GB at the same time ;) )